-
Latest Version
-
Operating System
Windows XP / XP64 / Vista / Vista64 / Windows 7 / Windows 7 64 / Windows 8 / Windows 8 64 / Windows 10 / Windows 10 64
-
User Rating
Click to vote -
Author / Product
-
Filename
nmap-7.50-setup.exe
-
MD5 Checksum
2d61a6bd20ff8a699abfecc582b27724
Sometimes latest versions of the software can cause issues when installed on older devices or devices running an older version of the operating system.
Software makers usually fix these issues but it can take them some time. What you can do in the meantime is to download and install an older version of Zenmap 7.50.
For those interested in downloading the most recent release of Zenmap or reading our review, simply click here.
All old versions distributed on our website are completely virus-free and available for download at no cost.
We would love to hear from you
If you have any questions or ideas that you want to share with us - head over to our Contact page and let us know. We value your feedback!
What's new in this version:
[Windows] Updated the bundled Npcap from 0.78 to 0.91, with several bugfixes for WiFi connectivity problems and stability issues.
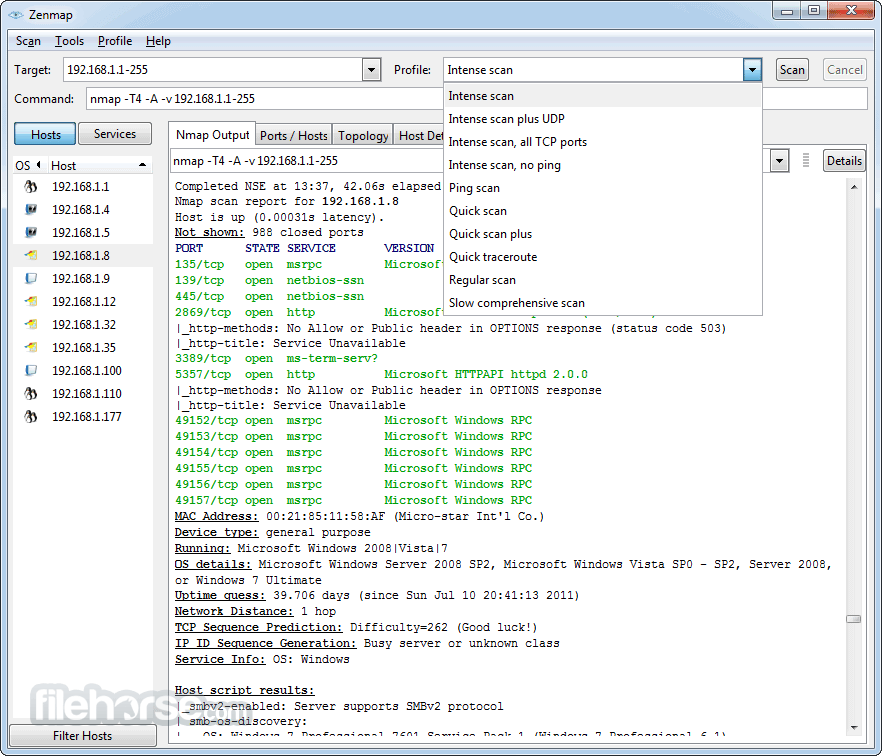
Integrated all of your service/version detection fingerprints submitted from September to March (855 of them). The signature count went up 2.9% to 11,418. We now detect 1193 protocols from apachemq, bro, and clickhouse to jmon, slmp, and zookeeper.
[NSE] Added 14 NSE scripts from 12 authors, bringing the total up to 566! summaries are below:
Broadcast-ospf2-discover discovers OSPF 2 routers and neighbors. OSPFv2 authentication is supported.
Cics-info checks IBM TN3270 services for CICS transaction services and extracts useful information.
Cics-user-brute does brute-force enumeration of CICS usernames on IBM TN3270 services.
Http-cookie-flags checks HTTP session cookies for HTTPOnly and Secure flags.
Http-security-headers checks for the HTTP response headers related to security given in OWASP Secure Headers Project, giving a brief description of the header and its configuration value.
Http-vuln-cve2017-5638 checks for the RCE bug in Apache Struts2.
Http-vuln-cve2017-5689 detects a privilege escalation vulnerability (INTEL-SA-00075) in Intel Active Management Technology (AMT) capable systems.
Http-vuln-cve2017-1001000 detects a privilege escalation vulnerability in Wordpress 4.7.0 and 4.7.1.
Impress-remote-discover attempts to pair with the LibreOffice Impress presentation remote service and extract version info. Pairing is PIN-protected, and the script can optionally brute-force the PIN. New service probe and match line also added.
Smb-double-pulsar-backdoor detects the Shadow Brokers-leaked Double Pulsar backdoor in Windows SMB servers.
Smb-vuln-cve-2017-7494 detects a remote code execution vulnerability affecting Samba versions 3.5.0 and greater with writable shares.
Smb-vuln-ms17-010 detects a critical remote code execution vulnerability affecting SMBv1 servers in Microsoft Windows systems (ms17-010). The script also reports patched systems.
Tls-ticketbleed checks for the Ticketbleed vulnerability (CVE-2016-9244) in F5 BIG-IP appliances.
Vmware-version queries VMWare SOAP API for version and product information. Submitted in 2011, this was mistakenly turned into a service probe that was unable to elicit any matches.
[Ncat] A series of changes and fixes based on feedback from the Red Hat community:
Ncat will now continue trying to connect to each resolved address for a hostname before declaring the connection refused, allowing it to fallback from IPv6 to IPv4 or to connect to names that use DNS failover.
The --no-shutdown option now also works in connect mode, not only in listen mode.
Made -i/--idle-timeout not cause Ncat in server mode to close while waiting for an initial connection. This was also causing -i to interfere with the HTTP proxy server mode.
Ncat in server mode properly handles TLS renegotiations and other situations where SSL_read returns a non-fatal error. This was causing SSL-over-TCP connections to be dropped.
Enable --ssl-ciphers to be used with Ncat in client mode, not only in server (listen) mode.
[NSE] NSE libraries smb and msrpc now use fully qualified paths. SMB scripts now work against all modern versions of Microsoft Windows.
[NSE] smb library's share_get_list now properly uses anonymous connections first before falling back authenticating as a known user.
New service probes and matches for Apache HBase and Hadoop MapReduce.
Extended Memcached service probe and added match for Apache ZooKeeper.
[NSE] New script argument "vulns.short" will reduce vulns library script output to a single line containing the target name or IP, the vulnerability state, and the CVE ID or title of the vulnerability.
[NSE] SNMP scripts will now take a community string provided like `--script-args creds.snmp=private`, which previously did not work because it was interpreted as a username.
[NSE] Resolved several issues in the default HTTP redirect rules:
- A redirect is now cancelled if the original URL contains embedded credentials.
- A redirect test is now more careful in determining whether a redirect destination is related to the original host
- A redirect is now more strict in avoiding possible redirect loops
- [NSE] The HTTP Host header will now include the port unless it is the default one for a given scheme
- [NSE] The HTTP response object has a new member, fragment, which contains a partially received body (if any) when the overall request fails to complete
- [NSE]NSE now allows cookies to have arbitrary attributes, which are silently ignored (in accordance with RFC 6265). Unrecognized attributes were previously causing HTTP requests with such cookies to fail
- [NSE] NSE now correctly parses a Set-Cookie header that has unquoted whitespace in the cookie value (which is allowed per RFC 6265)
- [NSE] NSE is now able to process HTTP responses with a Set-Cookie header that has an extraneous trailing semicolon
- [NSE] TLS SNI now works correctly for NSE HTTP requests initiated with option any_af. As an added benefit, option any_af is now available for all connections via comm.lua, not just HTTP requests
- [NSE] There is a new common function, url.get_default_port(), to obtain the default port number for a given scheme
- [NSE] Function url.parse() now returns the port part as a number, not a string
- No longer allow ICMP Time Exceeded messages to mark a host as down during host discovery. Running traceroute at the same time as Nmap was causing interference
- [NSE] Fixed a JSON library issue that was causing long integers to be expressed in the scientific/exponent notation
- [NSE] Fixed several potential hangs in NSE scripts that used receive_buf(pattern), which will not return if the service continues to send data that does not match pattern. A new function in match.lua, pattern_limit, is introduced to limit the number of bytes consumed while searching for the pattern
- [Nsock] Handle any and all socket connect errors the same: raise as an Nsock error instead of fatal. This prevents Nmap and Ncat from quitting with "Strange error from connect:"
- [NSE] Added several commands to redis-info to extract listening addresses, connected clients, active channels, and cluster nodes
- [NSE] Refreshed script http-robtex-reverse-ip, reflecting changes at the source site
- [NSE] Added 8 new http-enum fingerprints for Hadoop infrastructure components
- [NSE] Added two new fingerprints to http-default-accounts (APC Management Card, older NetScreen ScreenOS)
- [NSE] Fix for oracle-tns-version which was sending an invalid TNS probe due to a string escaping mixup
- [NSE] ike-version now outputs information about supported attributes and unknown vendor ids. Also, a new fingerprint for FortiGate VPNs was submitted by Alexis La Goutte
- Enabled support for TLS SNI on the Windows platform
- New service probe and match lines for the JMON and RSE services of IBM Explorer for z/OS
- Removed a duplicate service probe for Memcached added in 2011 (the original probe was added in 2008) and reported as duplicate in 2013
- New service probe and match line for NoMachine NX Server remote desktop
- [Zenmap] Fixed a recurring installation problem on OS X/macOS where Zenmap was installed to /Applications/Applications/Zenmap.app instead of /Applications/Zenmap.app
- [Zenmap] Zenmap will no longer crash when no suitable temporary directory is found
- [Zenmap] Zenmap now properly handles the -v0 (no output) option, which was added in Nmap 7.10. Previously, this was treated the same as not specifying -v at all
- Updated or removed some OpenSSL library calls that were deprecated in OpenSSL 1.1
- [NSE] Script ssh-hostkey now recognizes and reports Ed25519 keys
- [NSE] Fixed script hang in several brute scripts due to the "threads" script-arg not being converted to a number. Error message was "nselib/brute.lua:1188: attempt to compare number with string"
 OperaOpera 118.0 Build 5461.60 (64-bit)
OperaOpera 118.0 Build 5461.60 (64-bit) PC RepairPC Repair Tool 2025
PC RepairPC Repair Tool 2025 PhotoshopAdobe Photoshop CC 2025 26.5.0 (64-bit)
PhotoshopAdobe Photoshop CC 2025 26.5.0 (64-bit) OKXOKX - Buy Bitcoin or Ethereum
OKXOKX - Buy Bitcoin or Ethereum iTop VPNiTop VPN 6.4.0 - Fast, Safe & Secure
iTop VPNiTop VPN 6.4.0 - Fast, Safe & Secure Premiere ProAdobe Premiere Pro CC 2025 25.2.3
Premiere ProAdobe Premiere Pro CC 2025 25.2.3 BlueStacksBlueStacks 10.42.53.1001
BlueStacksBlueStacks 10.42.53.1001 Hero WarsHero Wars - Online Action Game
Hero WarsHero Wars - Online Action Game SemrushSemrush - Keyword Research Tool
SemrushSemrush - Keyword Research Tool LockWiperiMyFone LockWiper (Android) 5.7.2
LockWiperiMyFone LockWiper (Android) 5.7.2

Comments and User Reviews